The EBIOS Risk Manager method, promoted by the ANSSI, aims to support you in carrying out and monitoring your risk analyses. Discover here how the method is built, which workshops it includes and their objectives. To go further and start more concretely, use our Agile Risk Manager tool, certified for EBIOS Risk Manager by the ANSSI !
The origin of the EBIOS RM methodology
The EBIOS Risk manager (EBIOS RM) method was born from a reflection and an active collaboration between ANSSI and several major players, represented by the Club EBIOS. It comes from the experience accumulated over many years, and new needs allowing risk analysis to remain a relevant and effective tool.
Since the EBIOS 2010 version, the normative and regulatory framework has evolved a lot. Feedback has also pointed out certain limits and changes in practices, which have led to the definition of the new EBIOS Risk Manager method. Based on proven concepts, such as the notions of support assets and dreaded events, it has updated the approach and risk analysis work with current issues. By taking into account the functioning of organizations, the relationships with their ecosystem, etc., risk assessment goes beyond mere technical facts.
From now on, cyber security must be seen as a major axis of strategic and operational issues for any organization.
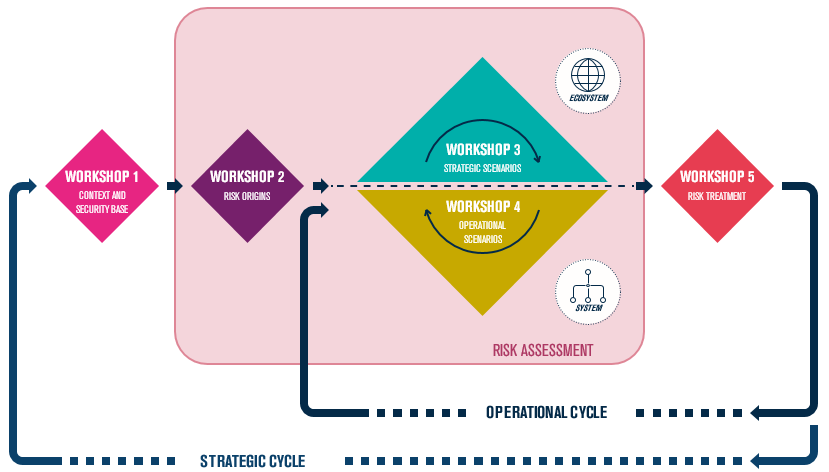
EBIOS RM : One method, 5 workshops
An agile and collaborative method
The method has been designed with the collaboration of experts and is intended to be evolutionary: it must live with its field and not remain static. This agile principle can be found in the very application of the method for carrying out risk analyses.
Indeed, the division into workshops allows the method to be approached like a toolbox. This allows us to focus only on activities related to the expected objectives. Conducting the workshops in groups is also a strong value in relation to agility and valuing the collaboration of the different trades.
In few words , we will use the EBIOS RM method for :
- Implement or reinforce the digital risks management
- Understanding and treate risks of a digital project
- Define a security level well suited for a project
Workshop 1 : Scope and security baseline
This first workshop serves to lay the foundations of the analysis, explaining its objectives, its framework, the participants in the different workshops and their roles. The selection of the expected objectives for the analysis specifies the other workshops that will need to be conducted.
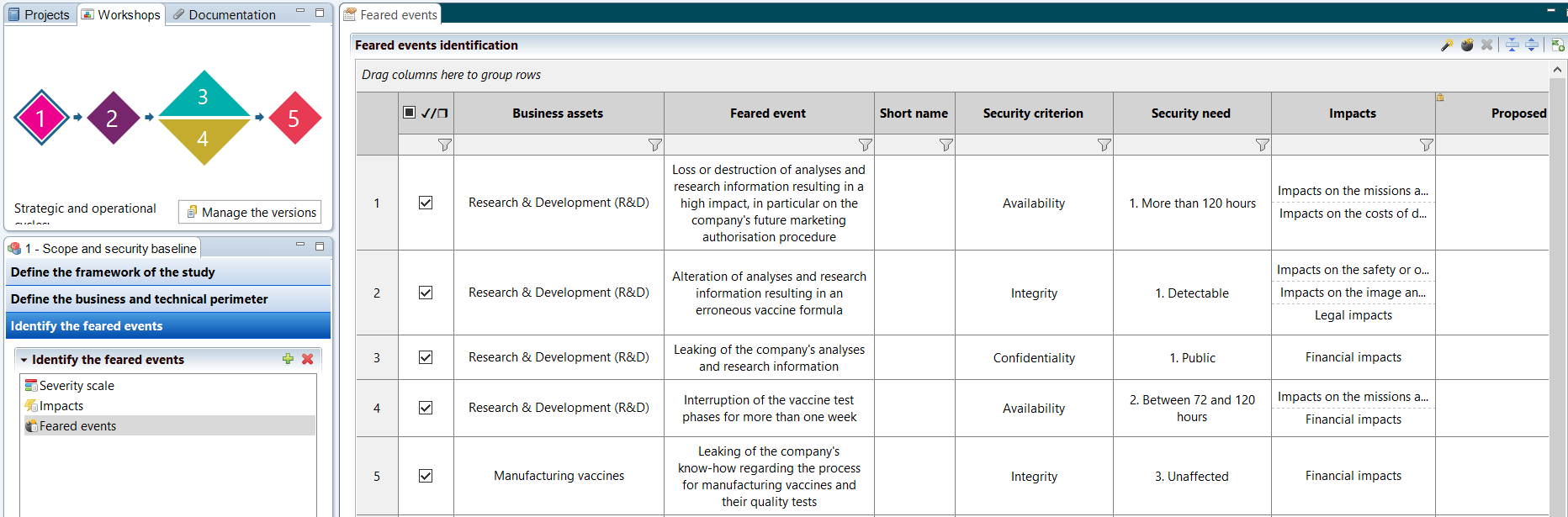
A second activity of this workshop consists in describing the business and technical scope to be taken into account, by describing the missions of the object of study, its support assets and its business values.
Following this, it is possible to define the dreaded events related to these business values, and to evaluate them in terms of impact and severity. Workshop 1 ends with the study of the security base, which allows, with a compliance approach, to eliminate the most obvious scenarios, by specifying the applied security references and by justifying the known potential deviations.
Workshop 2 - Risk sources
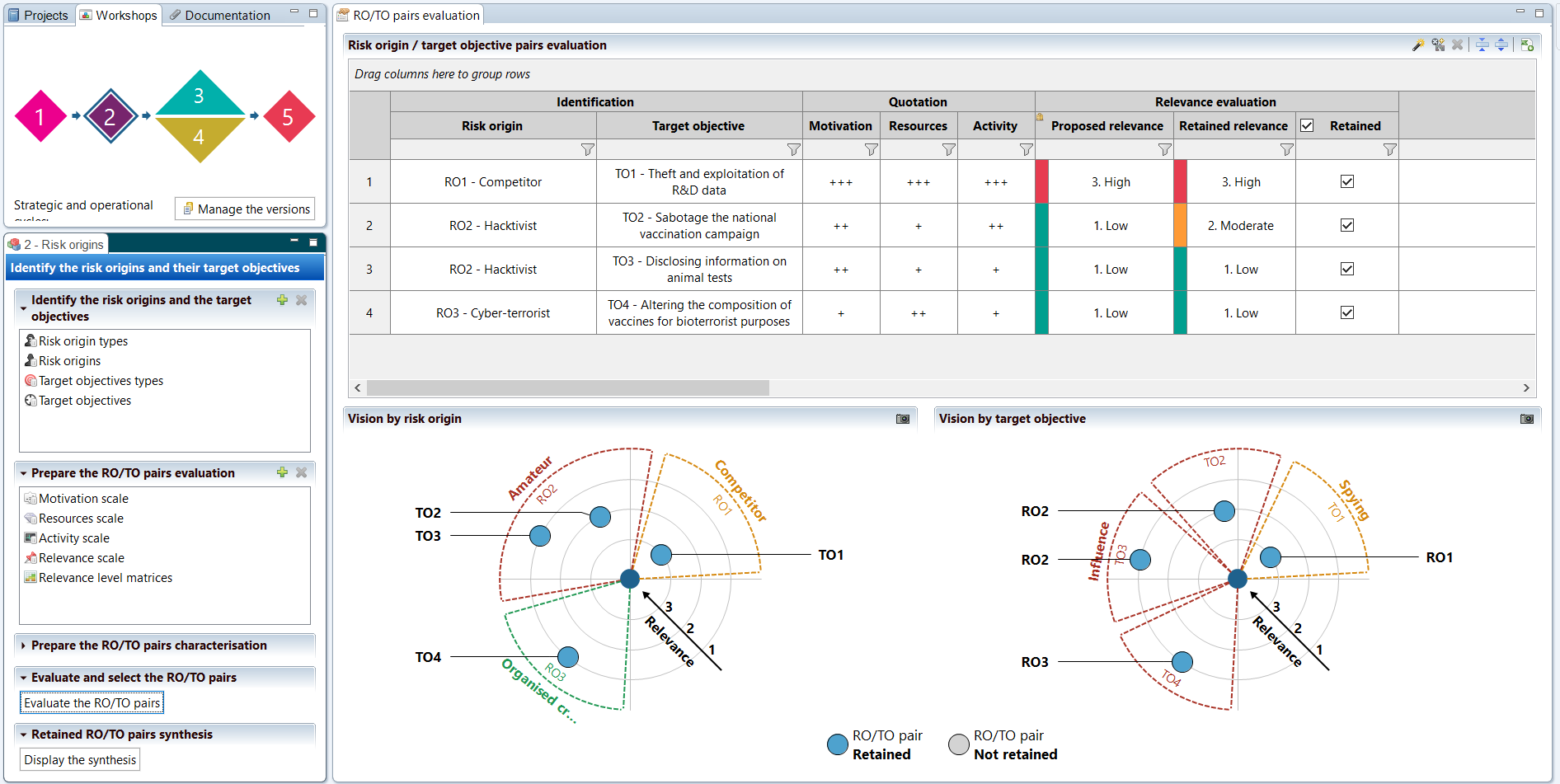
Workshop 2 proposes a targeted study of the sources of risk and the intended objectives, in order to determine representative cases that will make it possible to identify who may want to harm or attack the object of the study, and especially for what purpose.
This notion of couple is crucial to identify relevant cases. As everywhere in an EBIOS Risk Manager study, it is requested to work on a representative subset rather than seeking for exhaustiveness. The evaluation of the relevance of each couple is also based on an assessment of several criteria such as motivation, resources and activity of the risk sources.
It is also possible to use advanced threat intelligence elements to characterize couples by providing information on known weapons facts, specific modus operandi, etc. The information can be used to determine the relevance of each couple.
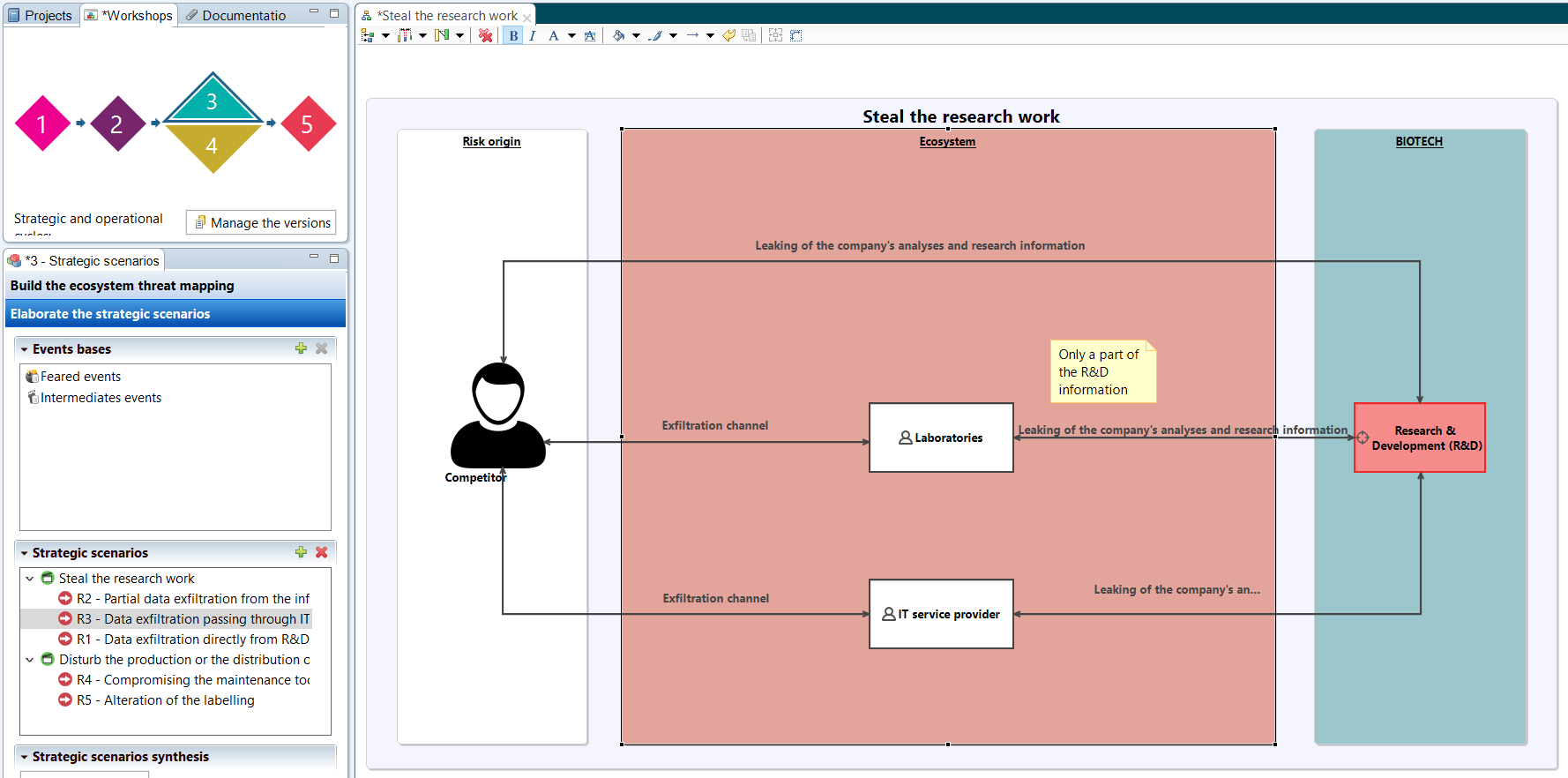
Workshop 3 - Strategic scenarios
During Workshop 3, a first activity is to map the threat that the ecosystem may pose. Indeed, taking into account the clients, partners or service providers who interact with the object of the study makes it possible to become aware of the threat they may represent.
This threat indicator is calculated according to the degree of dependency on this stakeholder as well as its reliability. Of course, this rating has little direct meaning, but it must be taken in a relative way, to compare the risks of each link in the chain.
Finally, once the ecosystem has been assessed, the second activity consists of graphically developing the strategic scenarios for each risk source/objective pair. These can be direct or involve one or more stakeholders, highlighting how the ecosystem can be used by an attacker.
Finally, thanks to these initial results, it is possible at the end of the workshop to propose security measures to be applied to the ecosystem to reduce its threat level and directly address certain scenarios.
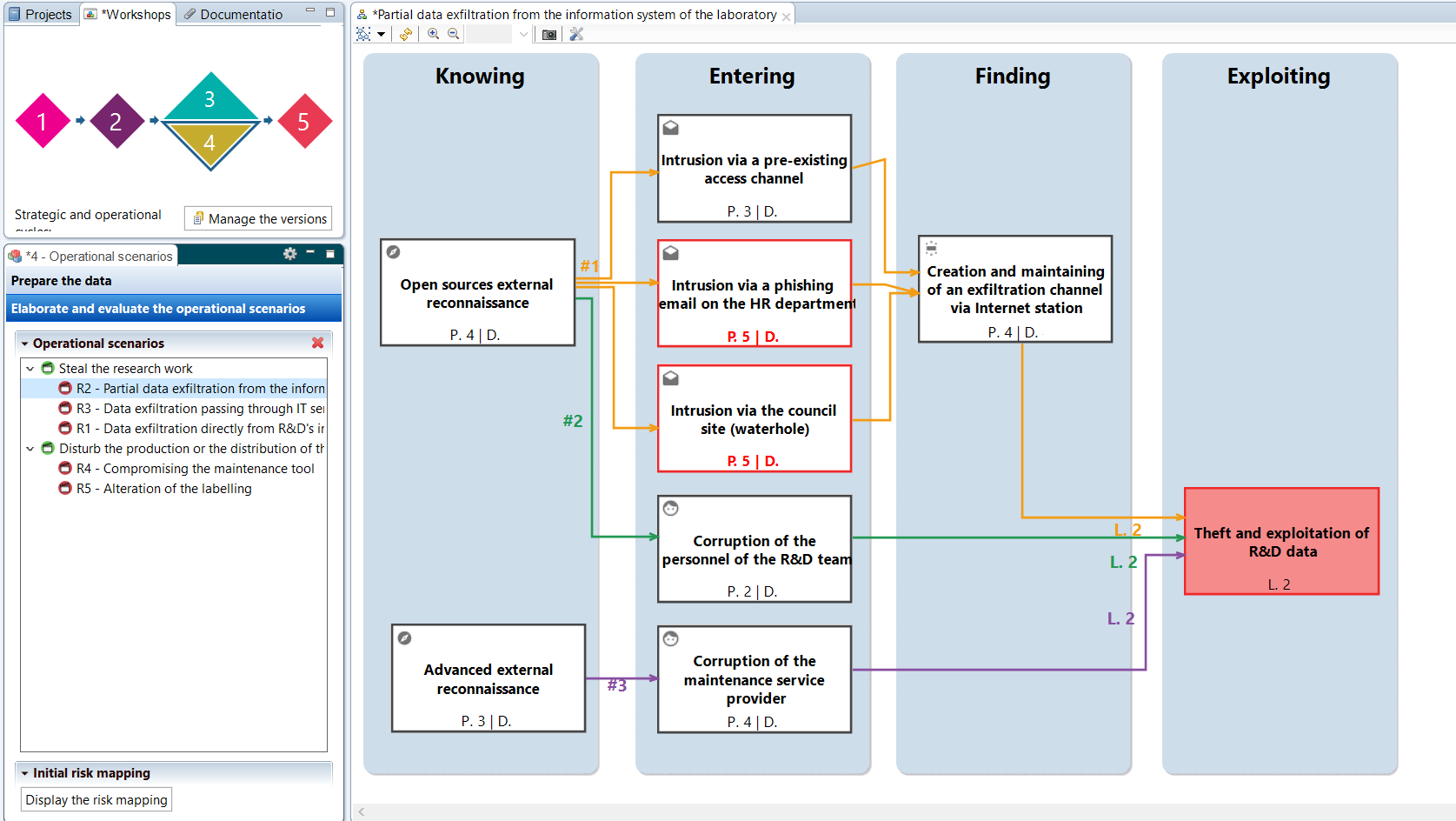
Workshop 4 - Operational scenarios
In addition to the strategic scenarios from Workshop 3, which remain high-level, Workshop 4 proposes to detail each possible path of attack and to represent them graphically in the form of operational scenarios.
The structuring of the scenarios is facilitated by using the phases of a “cyber kill chain”. These major phases show the organization of an attack, each of which may involve certain types of elementary actions. The latter represent the different stages of an attack, and can be linked to support assets, etc. to highlight the application in the context of the object of study.
Once described, the likelihood of each scenario can be assessed. The method proposes differents modes for assessing likelihood: from the most direct by rating the scenario globally, to the most detailed by taking into account the probability of success and the difficulty of carrying out each elementary action.
Finally, once the likelihood of each operational scenario has been assigned, a general vision of the initial risk is proposed through a global mapping.
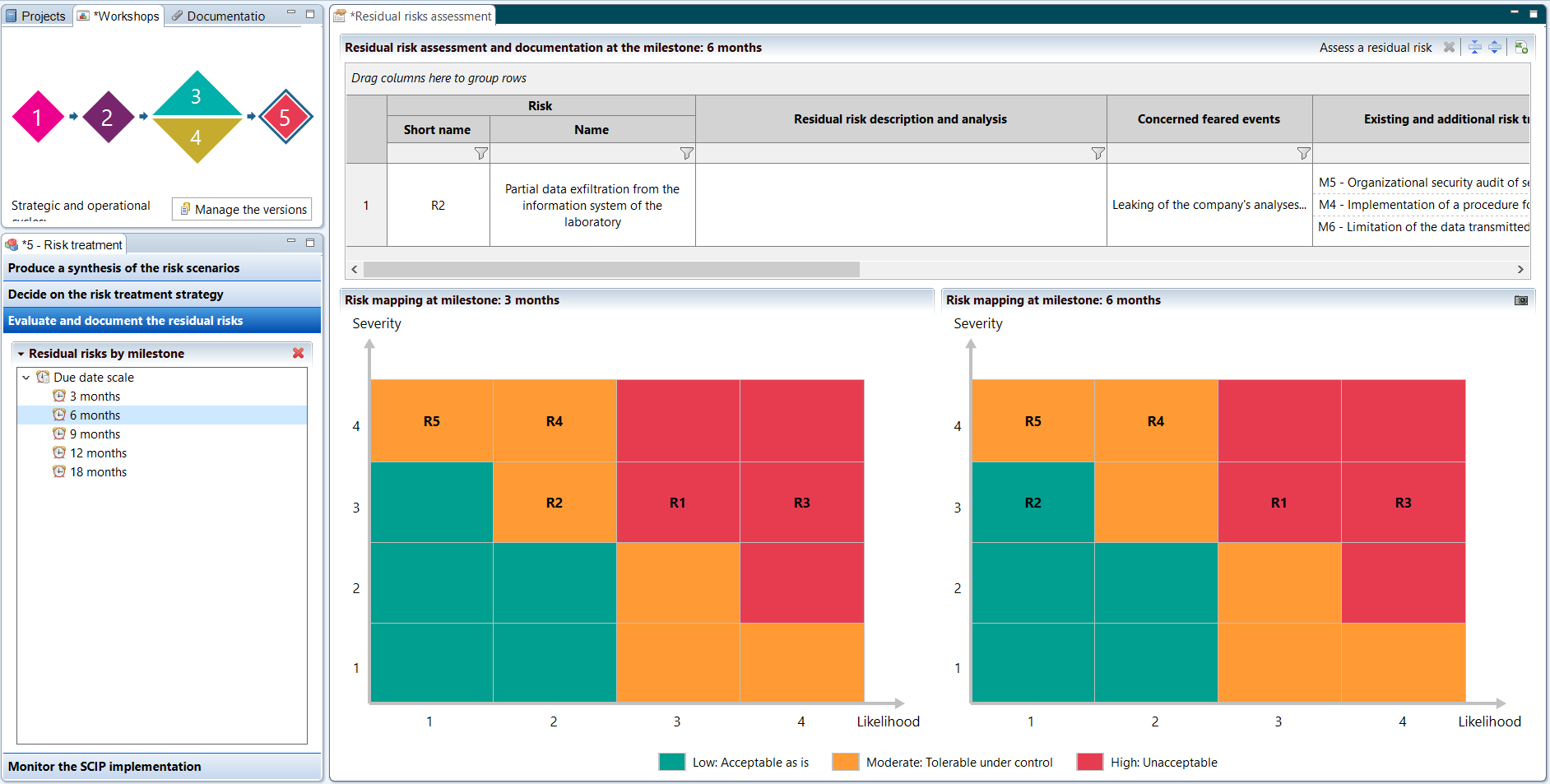
Workshop 5 - Risk treatment
Finally, workshop 5 intervenes last to deal with the identified risks and build a PACS (Continuous Improvement Plan). This vision of remediation over time is based on the agile vision of risk analysis and the iterative implementation of safety measures.
Indeed, thanks to the various assessments and results from the workshops conducted upstream, the PACS allows to target on which elements to act in priority, by building recommendations spread over several milestones. For each of these milestones, a level of residual risk emerges which may be considered acceptable or require new measures to be applied afterwards.